Beginner Level
Click on the Images in this Post to go to those Web Sites & Links
These are tools for the ISIS Hunters Toolbox
This method requires no knowledge of the issue. They have a online Data Base of known ISIS members web sites. it is a updated constantly 24/7. When a ISIS site goes down it is removed form the list. Read the details on their web site below for more info on how you can help by simply click on the twitter link and send report and then block it.
Lucky Troll Club
"WARNING: Profiles may contain extremely disturbing graphic images/"
This is a very helpful web site lots of helpful links. The link to the left * Here is the ISIS Block list. the following text is from that link
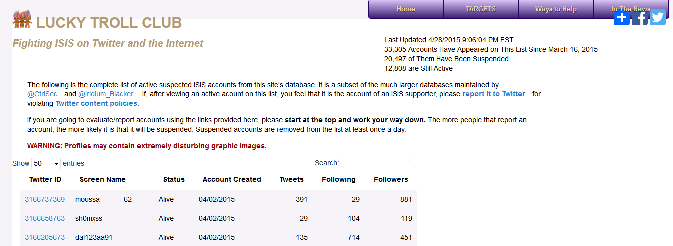
The following is the complete list of active suspected ISIS accounts from this site's database. It is a subset of the much larger databases maintained by @CtrlSec and @Iridium_Blacker.If, after viewing an active acount on this list, you feel that it is the account of an ISIS supporter, please report it to Twitter for violating Twitter content policies.
Click on the Images in this Post to go to those Web Sites & Links
These are tools for the ISIS Hunters Toolbox
This method requires no knowledge of the issue. They have a online Data Base of known ISIS members web sites. it is a updated constantly 24/7. When a ISIS site goes down it is removed form the list. Read the details on their web site below for more info on how you can help by simply click on the twitter link and send report and then block it.
Lucky Troll Club
"WARNING: Profiles may contain extremely disturbing graphic images/"
This is a very helpful web site lots of helpful links. The link to the left * Here is the ISIS Block list. the following text is from that link
The following is the complete list of active suspected ISIS accounts from this site's database. It is a subset of the much larger databases maintained by @CtrlSec and @Iridium_Blacker.If, after viewing an active acount on this list, you feel that it is the account of an ISIS supporter, please report it to Twitter for violating Twitter content policies.
If you are going to evaluate/report accounts using the links provided here, please start at the top and work your way down. The more people that report an account, the more likely it is that it will be suspended. Suspended accounts are removed from the list at least once a day.WARNING: Profiles may contain extremely disturbing graphic images.
OpNewBlood
This is a great source to really get up to speed on how to surf the internet safely. Everyoone who uses the internet should learn and know these basics/
Virtual Private Network (VPN) A virtual private network is a connection from your computer to
another network. Some of you may be familiar with these type of
connections as they are widely used by businesses to handle their
internal communications needs and to allow employees to access systems
from remote locations. Setup properly, they can also be used by anyone
to create a safer connection to the internet and have the added benefit
of disguising your true location. Click the link below for a short
tutorial on the different types of
OpNewBlood
This is a great source to really get up to speed on how to surf the internet safely. Everyoone who uses the internet should learn and know these basics/

No comments:
Post a Comment